Vendor Response
During the disclosure process for the stored XSS vulnerabilities in Piwigo 15.1.0, the development team provided the following response:
"Adding HTML in a photo description is not a security issue. Only administrators can do it. Administrators can do much more intrusive actions. As long as only administrators can do it, it's not a bug."
"The only reason why we would remove HTML from user input for administrators would be to avoid such false security reports. There is absolutely no security reason to do it. Only to get less useless reports like this.
...
I don't see any security issue here."
Introduction
Piwigo, a popular photo gallery application, has been identified to contain several stored Cross-Site Scripting (XSS) vulnerabilities in version 15.1.0. These vulnerabilities pose a significant security risk as they allow attackers to inject malicious scripts into various fields, potentially compromising user data and the application's integrity. This blog post will outline the discovered vulnerabilities, their impact, and remediation strategies.
Vulnerabilities Identified
1. Photo Properties Stored XSS
The first vulnerability is in the Photo Properties section under /admin.php?page=photo-1-properties. Malicious payloads injected into fields like Title, Author, or Description are executed on any page where the properties are displayed.
- Steps to Exploit:
- Log in as an administrator.
- Navigate to /admin.php?page=photo-1-properties.
- Upload an image and edit its properties.
- Insert the payload:
- Save the settings and visit the image page (e.g., /picture.php?/1/category/6) to trigger the XSS.
2. Tags Management Stored XSS
The second vulnerability resides in the Tags Management section at /admin.php?page=tags. When creating a tag with a malicious payload, the script executes when the tag is displayed.
- Steps to Exploit:
- Log in as an administrator.
- Navigate to /admin.php?page=tags.
- Create a tag with the payload:
- Assign the tag to an image and view the image page to observe the execution.
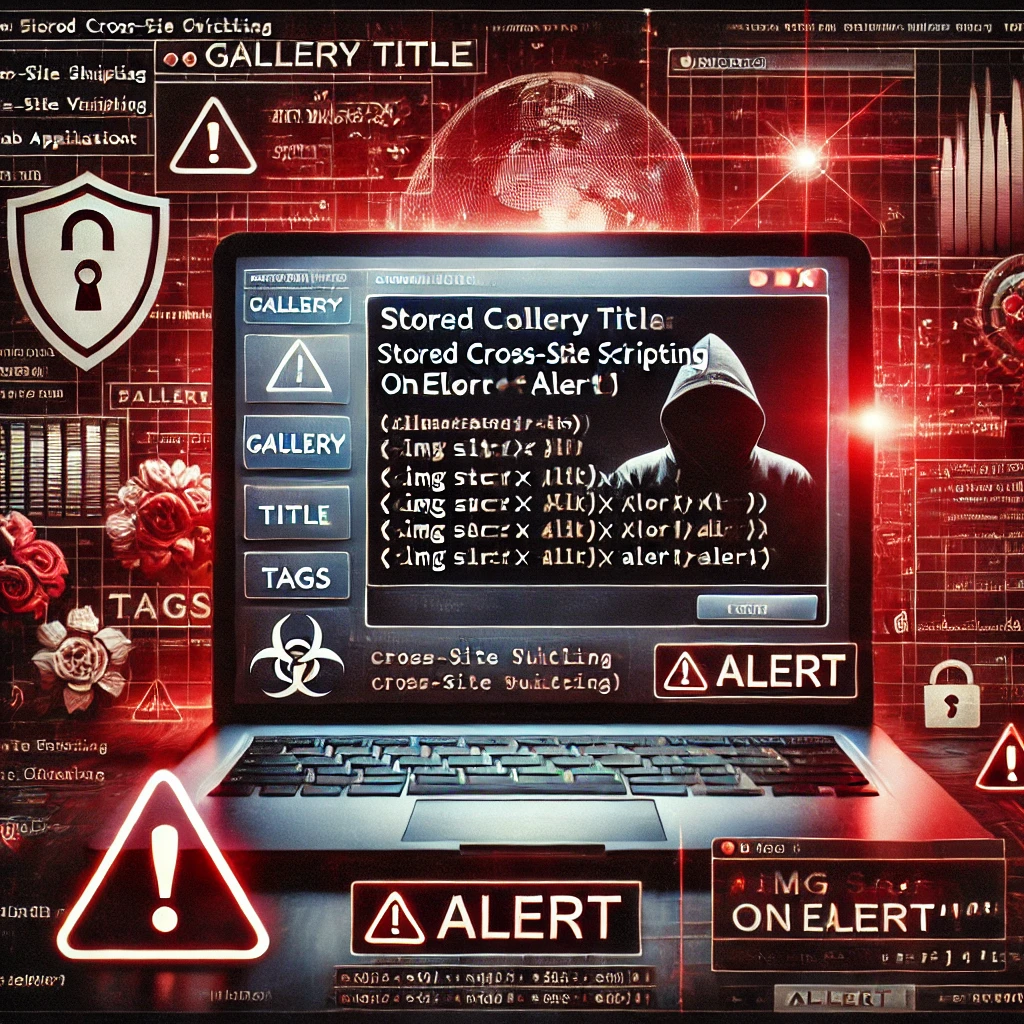
3. Gallery Title Stored XSS
On the configuration page (/admin.php?page=configuration§ion=main), the "Gallery Title" input field is vulnerable to XSS.
- Payloads: These payloads execute as scripts and can load external malicious resources.
4. Page Banner Stored XSS in "Elegant" Theme
In the "Elegant" theme, the "Page Banner" field renders raw HTML, enabling attackers to inject scripts.
- Payload: The malicious script is executed when the page loads, leading to arbitrary code execution.
Impact of the Vulnerabilities
The identified vulnerabilities can lead to severe consequences, including:
- Session Hijacking: Theft of user cookies and session tokens.
- Defacement: Unauthorized changes to the website's appearance.
- Injection of Malicious Scripts: Loading external scripts for further exploitation or malware delivery.
- Data Theft: Access to sensitive information from logged-in users or administrators.
Screenshots
Below are screenshots demonstrating the vulnerabilities:
Admin Panel XSS in Photo Properties
Tag Field XSS
Gallery Title XSS
Page Banner XSS
Recommendations
To mitigate these vulnerabilities, Piwigo administrators and developers should implement the following measures:
-
Input Validation and Sanitization:
- Strip or encode characters like <, >, ", ', and & from user inputs in all affected fields.
-
Output Encoding:
- Apply proper HTML escaping when rendering user-supplied input to prevent execution.
-
Content Security Policy (CSP):
- Add a CSP header to restrict inline script execution and external resource loading.
Example CSP:Content-Security-Policy: default-src 'self'; script-src 'self';
- Add a CSP header to restrict inline script execution and external resource loading.
-
Comprehensive Audit:
- Review all input fields across the application for similar vulnerabilities.
-
Consistent Error Handling:
- Implement Piwigo's "[Hacking attempt]" error message mechanism for all inputs to prevent improper data handling.
Conclusion
The discovery of these vulnerabilities in Piwigo underscores the importance of secure coding practices. While Piwigo is a robust platform, ensuring the integrity and security of its components is crucial for maintaining user trust. Addressing these issues promptly will not only protect the application but also safeguard its users from potential attacks.
By sharing these findings, we aim to raise awareness and encourage proactive measures to enhance security in open-source projects. Stay tuned for more insights and vulnerability analyses!