Vendor Response
The vendor does not consider this a vulnerability because only admin users have access to the site control panel. Admin users already have multiple ways to inject JavaScript, such as through fields explicitly designed for this purpose, like adding an analytics snippet to the header or footer. The vendor views this as intended functionality, and they believe it would only be a concern if it were available to less privileged users.
However, I disagree with this view for the following reasons:
Site Title Field Should Restrict Input to Text Only:
The "Site title" field is meant for text, not JavaScript. Allowing script injection is a misconfiguration that introduces a security risk, as seen in other CMS platforms that have addressed similar issues.
Impact on All Users:
The malicious script injected into the "Site title" field affects every page of the site. As a result, it compromises the experience of all users and visitors, extending beyond just the admin. This makes it a security concern that should not be overlooked.
I recommend restricting input to plain text and implementing proper HTML encoding to mitigate the risk and improve security.
Vulnerability Summary
A stored XSS vulnerability was identified in Plone CMS version 6.0.13. The issue resides in the "Site title" field under the Site Control Panel, where administrators can inject JavaScript code. This affects all pages on the site, leading to malicious script execution in the browser of all visitors.
Technical Details
The vulnerability allows attackers with admin access to inject malicious payloads into the Site title field. This payload is rendered in the <title> tag of the HTML <head> section across every page of the website.
Proof of Concept
Steps to Reproduce:
- Log in as an admin user in Plone CMS 6.0.13.
- Navigate to the Site Control Panel at http://localhost/your-site/@@site-controlpanel.
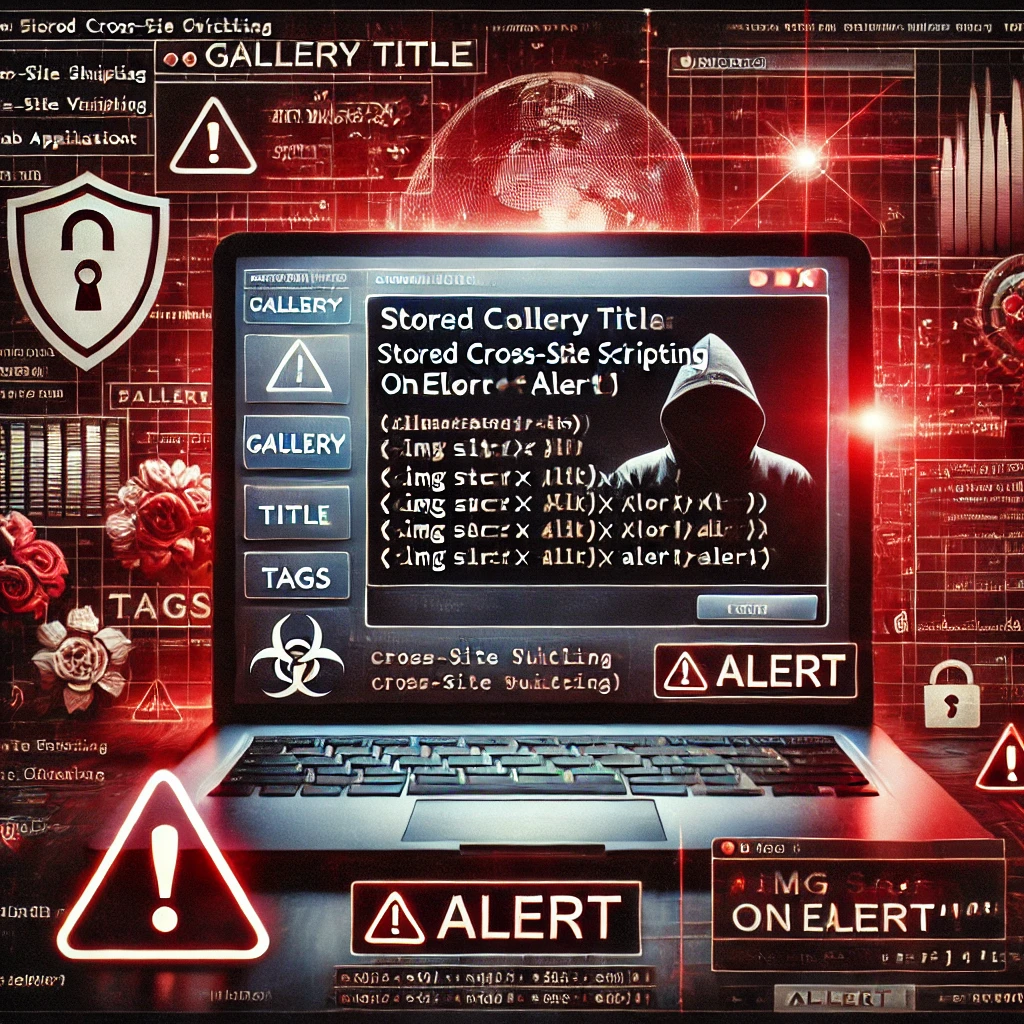
- Enter a malicious payload into the Site title field:
- Save the changes.
- Visit any page on the website as any user (authenticated or not).
- Observe the payload execution on all pages, affecting all users.
Screenshots
------------------------------------------------------------------------
Impact
- Global Script Execution: The injected payload executes across the entire site.
- Sensitive Data Theft: Attackers can steal user credentials or cookies.
- Browser Hijacking: Victims can be redirected to malicious sites.
- Reputation Damage: A compromised site loses user trust.
Mitigation Recommendations
Restrict Input to Plain Text: Ensure the "Site title" field only accepts plain text. JavaScript execution should not be allowed in this field.
Implement HTML Encoding: Apply proper HTML encoding for special characters to prevent potential script injections.
Access Control: Restrict site access to authorized users only.
Input Validation: Ensure all user inputs are properly validated to prevent malicious code injection.
Content Security Policy: Implement a robust Content Security Policy (CSP) to mitigate XSS risks.
Regular Audits: Conduct regular security audits to identify and address potential vulnerabilities.
User Awareness: Educate admins on the risks of improper use of input fields.
Timeline
- Reported: 21 NOV 2024
- Vendor Response: The vendor declined to consider this a vulnerability. 27 NOV 2024